
The Psychological Impact of Social Media Intelligence on Cyber Analysts
The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Published October, 2018
If you are reading this, you no doubt have read most of the alerts on LoJax the latest fun tool deployed by our friends from OPERATION KRAKEN or one of its groups APT 28. Since 2015 we have been tracking various types of APTs and Nation-State based technology that spills into cybercrime (we thought) and influenced new types of attacks that are harder and harder to detect with classical forensics and security solutions. We now have more confirmation from a third party completely neutral to us that helps us pass on some vital insights and 3+ years of research into what is really going on in cyberspace with regards to the links between APT28 and other groups out in the cyberspace espionage and cyberwarfare pandora’s box.
I don’t want to rehash someone elses work as ESET and some other researchers have great inital info about this new threat so I am not going to regurgitate what they already have posted about how this threat has an attack vector that pretty much targets firmeware level malware (a topic I have been talking about ever since VPRO came out..). Interestingly I looked into some of the websites that they are using to spread thier malware love on unsuspecting Mac and Intel Laptop users as well as Servers for better distribution and higher infection rates (We’ve seen this before right?).
In order for us to look at something not in the reports we need to view data from our globa sensor network to find and piece together the attack puzzle. In this case we take the TCP/UDP map and look at destination and source ports that the attackers use and are looking for. In short they are using variations in thier attacks that highlight different skill levels but also approaches to attacks (or profiles of attackers) in general so we need to assume there are other team members in this attack that is not just APT28 (yep you heard that right, its more than one group). Indications of muitple cultures and groups is something we have been looking to confirm for a long time and hence we recently published some initial research into what we call OPERATION KRAKEN. The interesting thing to mention is that the attacks are made to look like standard run of the mill attacks in some cases and seemingly unrelated to each other and simular time frame attacks, but when you collect data over a longer period of time and start to compare what many see as unrelated you see a trend. Its not AI its just comparing and looking, maybe some classification at best (thanks Thomas B!). So open-source or Bayesian and Neural networks with some of our Machine Learnig love is making things happen for real. This is analysis like we have never had previously but it also has its limits so you will always need a certain degree of human interaction to justify and confirm initial results with manual work. This doesn’t disqualify but rather enhances the data you get back much faster with this specially built, copyrighted and self-developed/engineered and tested solution.
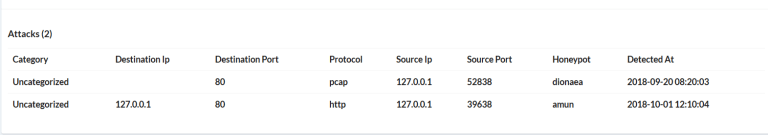
So lets take a look at some more data from an attack and we discover that we will see the destination ports are slightly different but still what we think is the same group based on common IOCs previously verified. Above we have the ports 52838 (apple xsan file system access) and 39638 an unassigned port. Is this a ruse or tactic to deter fingerprinting? Maybe, but we can’t ignore the fact that xsan ports are being used on Apple for file syncing and after seeing some of the new Apple targeting based malware surface in new attacks it is more than suspecious that you have two events right next to each other while most folks assume are not connected to each other (are they?). Maybe it’s the same campaign with different sub-groups doing various pieces of the bigger campaign? Some folks and groups that are using typical espionage tactics and hide in plain sight to make research all the more difficult or false positives? More research has to be done to connect more of those dots and really confirm this with data that confirms our thesis of this specific point (cooperation of multiple groups).
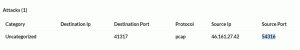
The picture however below of another (unrelated?) attack shows another port also used by Apple’s XSAN filesystem access (now we are starting to get corrilation of different events with same or simular IOCs, that is starting to show a trend and can not just be a coincidence? In this case however we don’t have a disintation port of 80 but rather the unassigned port of 41317. Maybe this is an IOC as well as scans from 52838 to filter or at least check in more details. What is rather disturbing about Apple ports (52838 and 56578) is that our last scan showed more than 194K hosts that were open on the internet and listing on those ports. If they are infected then thats a big infector / botnet of considerable strength. Maybe a good trend to observe….
Notice that the two attack source ports above are actually widely used Apple Ports for XSAN, etc. This is interesting as either they are using compromised Apple hosts to attack others or just making things a bit more interesting to throw researchers off the actual trail. Since we know IVAN lets assume the game of SnGs (I am not going to write that out here). The destination port in this case is 80 (http) but more interesting is the choice of ports used to go out. Whats even more interesting is that the IP belongs to the domain secao.org one of the domains involved in the very attack we are talking about with LoJax. We listed this site back in 2017 as an attacking site. What is more interesting is the links we can start to make by comparing older attacks with newer types of attacks, in this case cerber and locky. We stated previously that cryptocurrencies and other types of cybercrime attacks are not really cybercrime. Now with the report from ESET we can finally prove that from a third party’s finding of domains, matching those domains and all the risk intelligence we already do daily to find links to ransomware. We found more than 2000+ attacks
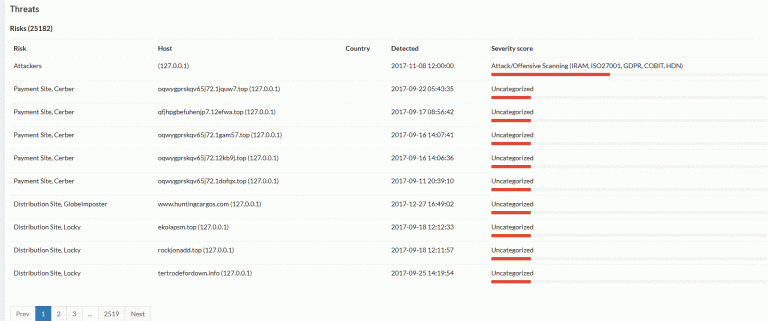
The picture above starts to compare more attacks and data we have been collecting since 2015 and the BlackEnergy 3+ attacks we found together with Soc Prime in Ukraine (and reported that to them) without even getting mentioned as the researchers who actually found it. Anyway we can start to match up attacks and data and start to cross reference this without having a SIEM system in place, the reason being that we are actually hunting and doing proactive analysis that does not fit into any SIEM space.
When we dig a bit deeper into IPs of one of the “known” domains we also get some interesting activties since 2016 that partially fit into Sandworm and BlackEnergy3+ / Firesale attacking vectors:
| 127.0.0.1 | 2018-09-30 21:36:24 |
| 35.177.67.15 | 2018-09-29 02:57:16 |
| 209.99.40.226 | 2017-11-27 14:44:34 |
| 91.134.203.113 | 2017-10-02 00:00:00 |
| 185.77.129.106 | 2016-11-13 00:00:00 |
Some of the intersting domains we found are:
These domains came in various configurations and additions like: oqwygprskqv65j72.17q8f6, etc. which I think we can agree fits into ransomeware infection tactics and are not or likely not normal business domains. Domains in typical ranges like .top and simular domains like Chinanet are hosting attacks more and more now that target simular types of attack vectors but confirming that both countries and APT groups are really linked in common campaigns is difficult at best (so far) to prove and almost imposible at worst due to multiple datasets that are just wrong or misleading. Data quality in this case for clasification is vital and a rare commodity that we are improving on through our unique approach to data usage/sharing by our customers and partners into actual risk intelligence.
A great out come for us is that the report from Eset confirmed we were the first ones to flag the site as malicous (back in 2017) which means that our approach is actually finding things that not ONE SINGLE AV company or cyber company found previously. At the time of another confirmation scan we only found about 5 companies that flagged this site in September and none of those were “standard” AV companies. The only two we found that are close are Sophos and Fortinet and then Forcepoint and two other companies DrWeb and CyRadar. This means only 5 other companies started to flag this site in September while we flagged this already in June 2016. We are not an AV company but this means that out functionality can certainly improve detection of non-standard and nation-state like vectors that no one else did until then.
Note: CyberNSight is not an AV solution, we don’t use signatures or heuristics but do use opensource mathmatics and classification (some refer to this wrongly as AI, it isn’t). We are finding things that others don’t and this result proves that we are doing something right which is great because now we can help others improve thier SIEMs, Firewalls, AVs and other solutions by integrating us in the hunting process.
I wanted to thank all the researchers out there that did great reporting and also got followed up by some of the newspapers and outlets, your tireless commitment (like ours) that mostly goes unpaid and under appreciated is what helps the world become more secure and learn.
If you want to contact me directly for press interviews, reports, partnerships and also as a customer to sign on to our services please just send an email to hakdefnet@protonmail.com or .ch
P.S. based on this attack and our research and forensics actvities that were greatly increased with CyberNSight we are now able to prove that cybercrime and cyber espionage, warfare groups are mixed together and likely in many cases the same actors. Some examples of the links we found are:
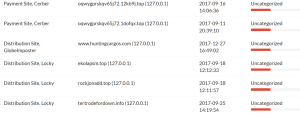
These are payment sites, distribution sites and ransomware campaigns inclluding Cerber, Locky and Globalmposter. We also have confirmation that malware loves certain hosting companies and also .top domains. We have data from these in our solution and our analyst service.
Your…. 1D10T
Copyright, Trademarks and Rights Reserved HDN and the Author. (2018)
References:
http://www.eweek.com/security/new-russian-malware-can-embed-itself-in-pc-firmware
https://www.digitaltrends.com/computing/lojax-uefi-rootkit-infect-machines/
https://www.bleepingcomputer.com/news/security/apt28-uses-lojax-first-uefi-rootkit-seen-in-the-wild/

The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Definition and Characteristics Stealth attacks refer to malicious activities that involve intrusions into computer systems without detection or raising alarms.
Sign up to get regular updates about security and special product promotions.
We value your privacy and will only use your email address for sending the newsletter. You can unsubscribe at any time.
For more details, review our Privacy Policy.