
The Psychological Impact of Social Media Intelligence on Cyber Analysts
The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Article date: September 2018 ~ See also: “Operation KRAKEN strikes again” -published 4th of January 2019
The entire world is facing one of the most comprehensive espionage and disruption campaigns in its history. Throughout our research we always found separate attacks that really had us scratching our heads because we saw so many different types of attacks that looked so similar and also cascaded with other seemingly unrelated attacks. With our new patented “VisiTak Technology” TM (M.Goedeker / Hakdefnet 2018) we have managed to break some of the mystery surrounding those attacks and the questions we had around them. For more details about this you will have to have a paid subscription and be a customer for the details. In short we visualize the threats and risks that we find in a way that brings back simplicity into security rather that make things even harder to understand than they really are.
Usually when firewalls and other types of permitter network devices collect data they look at (and actually need to wait) for attacks to actually happen in order to collect data that can be evaluated. This old mode of waiting for attacks to happen results in more breaches than ever before. We really started to wonder about how all these seemingly awesomely successful attacks always managed to target systems and areas that correlated to multiple exploits in underground markets as well as multiple vulnerabilities that were listed in places like MITRE and an the well known exploit-db sites. History showed previously that many attacks always leveraged comprehensive scanning tasks that triggered bans of those scanning IPs and then left only a partial picture to the attacker (from that IP) of what the actual target’s vulnerabilities actually are at the time of those scans. In some cases when attackers did not take the time to hide behind VPNs, Proxies or use someone else’s network (like a Starbucks or some other Cafe) then the attack was over or at the very least not destined to really be all that successful. In addition the victim was altered to the fact that someone might be targeting them (on the other hand ) in today’s haphazard security world that may not have really been interpreted correctly or in time to really stop the attacker.
The Arms dealers listed below are not a comprehensive list but they do add a certain amount of uncertainty in our cyber world simply because the market for exploits can range from $200 to more than $30,000 for certain Adobe and other similar exploits. While there will always be Cyber Arms dealers they also add a certain amount of destabilization into the world of cyber simply because their business model is obviously to find and resell exploits as well as tools that we see adverse reactions with on social media. Back in 2013/2014 Social Media BotNet platforms were being used to protect people and detect bad actors like terrorists but as time went on and the potential was seen for further revenue many of these types of companies sold their technologies that gave copies and access to some of the actors behind the Election Disruptions we see every day on Twitter, Facebook and other Social Media outlets. In addition many outfits build teams in an effort to build the perfect cyber weapon that avoids detection while still infecting the highest number of targets via stealth and interception tactics. Lastly some of these companies where so irresponsible with their own security that attackers finally breached them and released their technology into the open. As this happened we found out more about what they were really up to (you don’t know the half of it actually) and worse still those attackers in Russia and other countries like China have used the breaches to develop their own technology that was stolen or “copied” from those initial breaches. Since these companies are in effect not really regulated any weapons they create that gets breached can lead to any number of undetectable intrusions and spyware that is long deployed in cyber crime groups that have become much more tech savvy since 2014.
As time and attack technology move on we started to see evidence of coordination between data dumps, leaks, breaches and further attacks on leaked accounts, IPs and DNS records that were not in the same dumps but did appear in various unrelated dumps. When looking at the activities of Russian groups like APT28 we see massive attacks that target elections since 2015 using spear-phishing, tab nabbing (rewrite detected tabs with reroutes to compromised websites with drive by downloads) as well as evidence from CarbonBlue, Social Media OSINT and mixtures with groups like CyberBerkruit. When looking at the Turla group (another APT Group) operating in Russia and outside of it in France, Brazil, Germany, USA and UK (at least) via rented servers, we also see some trends in attacking techniques that seem to link both groups with each other.
The same signals seem to resonate with these assumptions when we start to look at the attack vectors that China’s APT Groups also use. We see evidence of Phishing attacks, backdoors and also wide spread use of RATs as well. In addition to the usual suspects we are also seeing a wide spread use of attack platforms that target Twitter, Facebook and LinkedIn users that leverage exploited accounts that are previously breached in an effort to social engineer potential targets using those platforms. Exploited or breached accounts are used to gather OSINT relevant information at then use this to find data that could be used to compromise new targets.
In General:
As we move into a more offensive and espionage technology based cyber crime and nation-state sponsored proxy groups that are paid to infect victims we also see new types of targeting of victims that was previously seen. Some of the data and Exploit based breaches on the darknet and underground forums shows newer types of access and attack vectors that seek to get and compromise targets private data.
In the screenshot below taken from one of those sites that has breached data we see access to a healthcare system that is in the US (keep in mind this is public data and we want to alert the person in this record that his data has been breached!). The screenshot is horrifying because many healthcare systems are being breached this very second as you read this post. The risk is real, the threats and exploits are being used and you may be targeted in this very way.
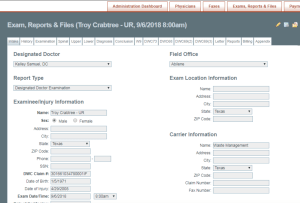
In addition to accessing the healthcare systems above we also find 110K+ breached accounts on all the usual Antivirus systems regardless of company and where they are from. Does this mean the systems are breached? Well in some cases they were, in other cases the breaches from previous years contributed to new breaches and exploited systems all the time, every day on every technology.
Not because I am saying this is it happening but people need to realize that attackers don’t sleep, they find breaches every day and they use them quickly. After those accounts are used they are dumped all over the internet and to other groups. So in this case all I have to do as a nation-state targeting you is wait for your data to get dumped, then I am in your system. If that takes too long then I will hire someone to do that work for me. IN the meantime that attacker can connect to any proxy or vpn and you have no real clue who it is without further analysis.

So what does all this really mean to you the reader? Well we can start with some of the technical reasons why disruption of elections is possible was intact due to a mixture of unregulated cyber arms dealers and breaches of those dealers. IN addition the training for using those tools and tactics required a different mind-set than what traditional security teams initially had. Sure you also learn about Blue and Red Teaming and Networking but hacking into clients, smartphones and other devices was done in a stealthy manner because you don’t want to raise any alarms. For all I know this computer is already breached and some nation-state is watching me write this right now…
To defend yourself you must understand your enemy and they want to hide in plain sight, use tools that others use to not arose suspicion then use hidden sources and exploits that no one knows about in order to get into your data and assets. This is the reality of security, one that most cyber security companies have no clue about simply because they never worked in this space and its also the reason why their technology is destined to fail over and over again. Its time to change the narrative and fight fire with fire.
CyberNSight was build with this situational awareness in mind because I worked in this space before and know some of the very people that write these exploits. They are smart, really smart and not your average script-kiddies. This is not a scare tactic its business, so wake up, look at the signs, get smarter on defense via risk intelligence. And for heavens sake start trusting smaller shops that have worked in this space. We know a few folks and some are out of work that are some of the worlds best code writers, if you don’t hire them someone else will…
(1D10T / M.Goedeker MSc.)
https://www.openwall.com/presentations/PHDays2015-john-devkit/slide-27.html
https://aptnotes.malwareconfig.com/web/viewer.html?file=../APTnotes/2014/apt28.pdf
https://securelist.com/analysis/publications/65545/the-epic-turla-operation/
https://www.icebrg.io/blog/footprints-of-fin7-tracking-actor-patterns
https://securelist.com/blog/incidents/57647/the-red-october-campaign/
http://kasperskycontenthub.com/wp-content/uploads/sites/43/vlpdfs/theteamspystory_final_t2.pdf
http://www.welivesecurity.com/2015/11/11/operation-buhtrap-malware-distributed-via-ammyy-com/
http://itlaw.wikia.com/wiki/Moonlight_Maze
https://www.govcert.admin.ch/blog/22/technical-report-about-the-ruag-espionage-case
https://lookingglasscyber.com/wp-content/uploads/2015/08/Operation_Armageddon_FINAL.pdf
https://www.threatconnect.com/blog/russia-hacks-bellingcat-mh17-investigation/#.V-wnrubaeEU.twitter
http://www.mcafee.com/us/resources/white-papers/wp-operation-shady-rat.pdf
http://cdn0.vox-cdn.com/assets/4589853/crowdstrike-intelligence-report-putter-panda.original.pdf
http://www.crowdstrike.com/blog/whois-numbered-panda/
https://www.fireeye.com/blog/threat-research/2015/12/the_eps_awakens.html
APT Gang Branches Out to Medical Espionage in Community Health Breach
http://securelist.com/blog/research/57585/winnti-faq-more-than-just-a-game/
http://blog.trendmicro.com/trendlabs-security-intelligence/winnti-abuses-github/
http://cybercampaigns.net/wp-content/uploads/2013/06/Deep-Panda.pdf
https://securelist.com/analysis/publications/69953/the-naikon-apt/
https://blogs.technet.microsoft.com/mmpc/2016/04/26/digging-deep-for-platinum/
https://securelist.com/blog/research/70726/the-spring-dragon-apt/
CrowdCasts Monthly: You Have an Adversary Problem from CrowdStrike

The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Definition and Characteristics Stealth attacks refer to malicious activities that involve intrusions into computer systems without detection or raising alarms.
Sign up to get regular updates about security and special product promotions.
We value your privacy and will only use your email address for sending the newsletter. You can unsubscribe at any time.
For more details, review our Privacy Policy.