
The Psychological Impact of Social Media Intelligence on Cyber Analysts
The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Article form April 2017
Everyone in “cyber” and “security” is now talking about how they could have stopped WannaCry and ransomware in general. Depending on which companies posts, updates and documents you read to this specific type of ransomware the reality is that MalwareHunterTeam (@malwrhunterteam) discovered and (@MalwareTechBlog) stopped WannaCry by accident (btw,awesome work guys!).
After the last post I did that addresses some key issues and challenges 90%+ of companies actually face (this is based on) the fact that we do research and also projects that implement SOC, NOC, SIEMs and all other kinds of security event reporting and monitoring solutions since these can use our risk intelligence solution CyberNsight / NeedleStack.
Its always easy to blame customers and partners for breaches, however I don’t really think this is productive nor does it lead to those organizations implementing someone’s product or getting better. If you sell based on blame, FUD, and fear then I would not wonder if those companies actually do nothing or tell that salesperson or company to take a hike. Granted, there are always going to be companies that don’t see the value of security or implementing product x,y,z and to be honest they are very often right.
This “cyber attack” which it wasn’t btw (I’ll explain later) shows us that we need a more proactive and 180 degree way of training, designing and implementing security operations and solutions. It also shows us that many companies just don’t have the right partners selling them yet another AV (AntiVirus, UTM, Firewall, SIEM) while these are absolutely components of secure operations they are not a singular solution to WannaCry or any other ransomware infection. I have been a big fan of a few things I teach i every training (wether MOC or any other engagement):
Proactive Security Teams
The Principle we created way back when in the 90s (MiGo Tech) was very simple. Hacking is a great way to do forensics, analysis and threat modeling. These teams tend to have a more proactive approach to Risk Management, Threats and also Security.
Teams have active members that breach internal systems in order to assume or predict possible entry points into a network or the companies systems and while these sounds costly in reality it is not. If you calculate the costs for buying all the “security stuff” you currently have and evaluate the value of those things, do you see a trend in reduced attacks that are successful?
Do you see that risks are mitigated as a result of those solutions or products? Does it help you find new risks or new types of information and intelligence that is really useful to you, the team and the company? These are some important questions to ask for any investment into a suspected silver bullet solution or “SSB’s” as I like to call them. The difference (I believe) in finding threats is also understanding how they are used or exploited.
This knowledge combined with research tools, and modified forensics principles can speed up the process of finding the “un-findable” is the basis for my research and CyberNsight. I realized that spending so much money on services like Shodan and Threat Feeds did not actually help in the Pre-Attack phase or in identifying where the next attacks were going to come from.
This prediction required a lot of manual research which companies did not see the value in paying for or had the awareness, skills or capability of building up. If we add the fact that many threat feeds are actually free (and this had me wondering many nights why “cyber” companies charged 300k+ for them) then the question quickly becomes how these really add value to prediction and then detection. Both components need people, processes and procedures to work correctly and efficiently. Lastly we have the factor time, resources and skills. All are vital to finding those needles in haystacks.
Threat Types have evolved with the times! In the picture below we see that threats have evolved with electronic weapons and attacks. These iterations in attacks lead to new threats that then require new skills to detect, analyze and stop. Each time a new type of attack shows up, teams must understand the details of those newt attacks and adapt their training, analysis and detection for new indicators of compromise (IOCs).
One thing to note is that new attacks do not always mean completely new vectors, in the case of MitM and SQLi, these attack vectors as well as Phishing have become more targeted based on OSINT and Intelligence information that an attacker or the attackers teams collect from targets, industries or countries.
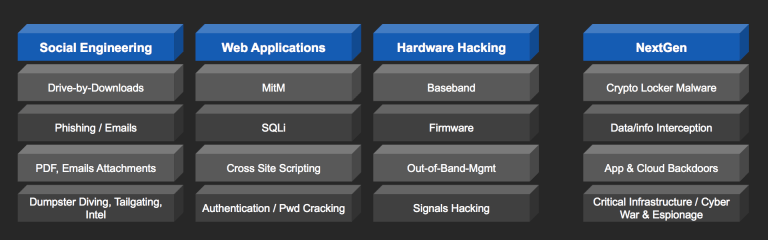
Evolving threats also leverage specific areas initially than then also evolve with new attacks to “exploit” other human or organizational weaknesses that previous attacks may have identified as lessons learned from previously unsuccessful and successful attack vectors.

Actionable Intelligence
This concept should not be new to anyone that has been in the military and will also likely be logical in that we assume that any intelligence, data or component that we use to collect intelligence needs to be trustworthy, available and timely.
When a solution or product does not seem easy to use (relevancy to the process itself) then the question becomes how is the data we collect, process or store even relevant to operations, security and the company or customer’s customers?
We collect data for a reason, usually it is to build awareness and then create defenses and detection rules and actions in case of an attack and if successful, detecting the attack was successful.
Predictive Risk Intelligence Approach (CyberNsight)
In predictive risk intelligence, our objective is to learn from what we collect quickly in order to predict or calculate were the next threats or risks really are. This is a part of the classical intelligence phase in military and intelligence agencies use to “scope out” a HVT (High Value Target).
When a nationstate or hacker group wants to find out about a target in its campaign, it looks for risks that can be threats, threats that can be exploited and exploited systems that can lead to the “motherlode” or goal, data, etc. What predictive risk intelligence and analytics really does is help you map risks, compare with evidence and then use that really early information to test theories, probe systems and see who is collecting what and how your risk exposure really is to the world at large.
Being predictive takes a new approach to threat and risk detection and deterrence. There is no fanciness to this, its hard work and takes time. This is were we come in, after implementing all kinds of SIEM, IDS, IPS, UTM and whatever they call the technologies of AntiVirus and Threat Intelligence Feeds today, they are not predictive in nature.
Even if “sandboxing” is sold as the next best things, risks are not detectible if they don’t have some type of signature or behavior pattern that can be matched with a database. This is why being predictive makes the most sense, if you can see threats and risks as they are being created and tested, you are way ahead of the game here.
Our solution in this case speeds up analysis of risks by up to 90%, leaving the last ca. 10% already analyzed so that teams and partners can concentrate on the highest likelihood of potential risks based on the multiple types of data we collect via our own sensors and technology as well as OSINT tools that we obviously don’t charge for because they are open source…
What we do charge for is pre-analysis, data collection standardization, push API and proactive search technology and engines.
Our Risk Intelligence Training System (NeedleStack)
Our specific training system leverages the unique approach and our solution to predictive risk intelligence, showing users, companies and entities how they can use our platform to speed up the process of risk identification and then export those findings to any system like SIEM, Log Management, GRC or any other type of console or systems the customer may have.
There are also pre tested scripts, queries and areas that we recommend to look at in order to find new and evolving attack groups, campaigns and software that may be relevant. Lastly we show customers how to build searches that result in analyzed and scored results that provide tangible results to potential risks and attacks before they actually happen.
Some components that we look at are:
Scoring returned results (some say proprietary, we say Bayesian, Neural or Probabilistic Analysis)
After using our patented and copyrighted approach (HDN, M.Goedeker 2017) we then use all the information and analysis options that we have to score results and find out probabilities of results being relevant to the customer or team.
We have our own solution that enables detailed analysis, flexible scoring and reports as well as exported findings via API and other file types to any solution that can read those file types. The possibilities are endless when you consider that the entire system is open to various types of data, analysis and scoring can be dynamic or customized. We believe this is the worlds first predictive risk intelligence engine (PRIE).

Details on how WannaCry works
The picture which is taken from the user @CyberAppy shows some details on how the specific initial version of WannaCry works and is executed.

My initial Scan of Ransomware before WannaCry
I did multiple talks last week before WannaCry actually happened to show people how you would go about looking for Ransomware risks and the search (1level) took about 1-2 seconds to come back with results.

Keep in mind that you will want to look on the DarkWeb for potential threats as on the normal net you will find may “hits” that are marketing and not necessarily relevant for your search and analysis. The reason for this is that groups that really know what they are doing will “typically” not want you to find them and their work before its released or sold to the highest bidder.
Related to this hacking into multiple social media accounts is another item you can find very easily on the Darknet.
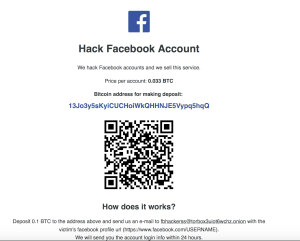
If you like what you have seen and understand the value of this powerful solution, lets have a discussion and figure out how to implement NGSD (next generation security defense).
(so thats it for this post, if the stuff was interesting and adds value please let me know and email us at support@hakdefnet.com)
(As always this post, the information, our solution pictures and website are subject to copyright 2017 Hakdefnet) Other pictures are copyright their respective authors.
Update, one of the folks that sinkholed the domain that caused WannaCry saw an attempt via China to steal the domain. Wether this means China is behind it is still way to early to say but its certainly an interesting piece of info. The pastebin link from @MalwareTech is here: https://pastebin.com/r5fh2GxL
The link to IP info is here: http://ipinfo.io/106.121.2.55

Looking at the details of the IP in net craft we see the following information:

As you can tell, there really isn’t much data to go on but the resource that attempted the domain takeover was in fact from a China IP. More detailed analysis would be great to see if this IP turns up in other attacks and currently we did not have any hits previously in other attacks that we have seen. The network is however very active and similar IPs did show up in other ransom ware attacks, what this means, not conclusive yet….
In addition there is also a Bot on twitter (@ransomtracker) that looks at payments to the wallet associated to the WannaCry ransom ware:

We are providing a free social media followers list of the ransom tracker bot so that you can see who is following the bot. If there is a user you associate with the ransom ware please let us know and we can do a detailed analysis.
| name | followers_count | friends_count | statuses_count |
| _Ambr_ | 99 | 535 | 25 |
| S4nta_ | 7 | 30 | 163 |
| PCDUE | 1104 | 1083 | 90374 |
| TinyTarrasque | 130 | 142 | 11002 |
| andremattosamr | 15 | 875 | 58 |
| baldengineering | 4 | 14 | 29 |
| Castromuff | 130 | 867 | 287 |
| mbaines3 | 371 | 763 | 120 |
| JeanFMascari | 25 | 261 | 50 |
| Eng_HishamAdel | 610 | 2794 | 25967 |
| oskahenri | 0 | 24 | 11 |
| agotthardsson | 10 | 58 | 7 |
| britesense | 145 | 250 | 8302 |
| Antonio75449285 | 10 | 227 | 5 |
| oNFNFo | 135 | 319 | 1088 |
| LorenAgostini | 7 | 52 | 30 |
| nasrulseven | 81 | 25 | 138 |
| NotGoxed | 188 | 430 | 1236 |
| AFoletti | 91 | 166 | 212 |
| MPhilDG | 34 | 316 | 117 |
| ionstorm | 866 | 2223 | 1607 |
| neil7nove | 238 | 534 | 313 |
| thijstriemstra | 271 | 487 | 3931 |
| EthanKesner | 478 | 503 | 561 |
| BrezaTZg | 0 | 15 | 0 |
| brianhalliday | 73 | 39 | 2238 |
| ChristianStich | 18 | 311 | 4 |
| zergless | 279 | 799 | 4920 |
| runsecbit | 43 | 205 | 238 |
| neutrinoguy | 39 | 440 | 54 |
| joaquinpr81 | 10 | 41 | 3 |
| rdasm | 427 | 1941 | 2044 |
| JosephRaleigh | 44 | 421 | 486 |
| ivarivano | 869 | 1390 | 5737 |
| DarenSlick | 8 | 47 | 6 |
| evankaloudis | 1346 | 2819 | 11544 |
| deejmon | 1025 | 2361 | 871 |
| DeanKashlan | 7 | 49 | 0 |
| suqdiq | 1118 | 4286 | 30223 |
| devknob | 450 | 509 | 2862 |
| tomtom2770 | 12 | 85 | 8 |
| Jobeyond | 24 | 149 | 13 |
| rafaybaloch | 13406 | 346 | 4848 |
| fazio_antonino | 3 | 28 | 3 |
| sergioayalat | 130 | 319 | 108 |
| FarhoudSalimi | 13 | 36 | 1 |
| sukren | 91 | 106 | 4242 |
| JeSuisBilly | 45 | 383 | 579 |
| cplbrennanm | 18 | 100 | 23 |
| MarcoDaino | 119 | 397 | 286 |
| ValhallaSec | 14 | 754 | 12 |
| KBHR570 | 50 | 51 | 808 |
| tentativestate | 48 | 197 | 270 |
| SlackenerlyT | 0 | 1 | 0 |
| CarloZanutto | 32 | 49 | 42 |
| lucianocantaro | 132 | 339 | 679 |
| p13t40 | 0 | 7 | 0 |
| nioanto2 | 97 | 174 | 491 |
| GanetheGreat | 261 | 737 | 4147 |
| eclissedomar | 22 | 142 | 346 |
| cristi_vic | 835 | 977 | 3398 |
| vittoriov | 81 | 259 | 4845 |
| Lelecottero | 78 | 373 | 4262 |
| BlakeBaysinger | 1423 | 4972 | 600 |
| aocsym | 220 | 412 | 560 |
| AndreaSvizzero | 253 | 1647 | 6683 |
| franctarallo | 41 | 316 | 106 |
| ParisMaik | 165 | 786 | 365 |
| continimarco | 63922 | 63278 | 196302 |
| nonmipare | 11 | 125 | 463 |
| magicbaconman | 16 | 109 | 6 |
| NoCryptolocker | 702 | 359 | 91 |
| TaleGigi | 158 | 560 | 4024 |
| aj_charbonneau | 10 | 65 | 4 |
| emy77 | 94 | 413 | 1156 |
| eMediaIan | 10 | 124 | 237 |
| fncraffa | 24 | 135 | 89 |
| boucherhayes | 42898 | 1091 | 22115 |
| boxtoscana | 530 | 365 | 876 |
| ayaz_khan | 399 | 197 | 19109 |
| tribal_sec | 480 | 1259 | 2322 |
| BinaryBandit1 | 8 | 188 | 2 |
| The_Haiku | 905 | 854 | 1093 |
| raphaelcockx | 886 | 725 | 39112 |
| carlocapuani | 30 | 100 | 60 |
| ILiedAboutCake | 410 | 149 | 1370 |
| TGambart | 32 | 144 | 0 |
| _lmcy | 255 | 324 | 9125 |
| pierellozzo | 134 | 782 | 912 |
| jefferyluce | 114 | 482 | 662 |
| christoph08 | 25 | 76 | 7 |
| IsohanniJuho | 1 | 43 | 0 |
| xraul | 220 | 440 | 17087 |
| montecarru | 0 | 14 | 21 |
| cerebro84 | 766 | 1061 | 35048 |
| bkpap | 270 | 500 | 14774 |
| a_sure_seany | 448 | 366 | 19778 |
| zanicla | 29 | 134 | 43 |
| jameshooker | 343 | 653 | 4117 |
| A_Roqi | 907 | 453 | 1676 |
| henriksmoller | 17 | 47 | 59 |
| flowestack | 50 | 918 | 762 |
| Danny_Murphy_TA | 78 | 359 | 176 |
| mludwiszewski | 225 | 286 | 253 |
| giox069 | 37 | 53 | 77 |
| honoki | 413 | 817 | 5119 |
| MrBadGuy1981 | 50 | 180 | 715 |
| fabiomast | 50 | 71 | 850 |
| CyberElite7 | 194 | 1030 | 583 |
| ORARiccardo | 467 | 2475 | 17875 |
| daymon06 | 17 | 92 | 449 |
| dasderi | 33 | 314 | 1061 |
| saverioraz | 57 | 168 | 72 |
| r73lio | 93 | 186 | 1053 |
| scricciolo2 | 10 | 71 | 32 |
| dariofio | 7 | 17 | 2 |
| sudo_f | 97 | 932 | 1809 |
| wisekhan | 80 | 103 | 102 |
| felmoltor | 431 | 664 | 9476 |
| WearsTheFoxHat_ | 520 | 2225 | 23560 |
| emohawk | 160 | 651 | 4501 |
| irlionel | 235 | 958 | 440 |
| ruskin147 | 169607 | 4884 | 50883 |
| ThAOSteen | 4220 | 4354 | 159310 |
| botfrei | 1076 | 543 | 4481 |
| shonaghosh | 4362 | 2898 | 21747 |
| s_vvoorst | 213 | 399 | 76 |
| ofehrmedia | 496 | 666 | 7477 |
| infoturbekeskus | 51 | 50 | 98 |
| dalessandrini9 | 33 | 154 | 0 |
| queitsch | 255 | 985 | 8265 |
| danielsolisagea | 673 | 1432 | 3805 |
| GabyRasters | 1620 | 2358 | 19717 |
| ArildThorsby | 350 | 1416 | 1358 |
| louissschang | 284 | 238 | 826 |
| HaOz_Ong | 16 | 51 | 23 |
| HSCyberSec | 228 | 507 | 1764 |
| VictorPetrescu | 133 | 773 | 15 |
| booloki | 107 | 386 | 889 |
| UnderNews_fr | 5558 | 1003 | 21227 |
| AritzBi | 452 | 890 | 36329 |
| ChrisJangita | 490 | 447 | 1538 |
| RositaRijtano | 1075 | 2109 | 807 |
| TomReichhart | 7588 | 1679 | 3739 |
| dcarlisle08 | 156 | 357 | 1132 |
| LloydDavis | 5469 | 2145 | 31959 |
| olemoudi | 944 | 478 | 2378 |
| darrena0921 | 7 | 59 | 18 |
| spoonzy_ | 128 | 693 | 780 |
| Rockcena5 | 317 | 767 | 86 |
| alsajir | 5 | 15 | 20 |
| akilsrin | 199 | 301 | 75 |
| 0n1r1k0 | 81 | 384 | 571 |
| FelixWeis | 587 | 393 | 111 |
| 2funky | 40 | 60 | 240 |
| hayzeebaby | 3 | 41 | 0 |
| rrrhys | 465 | 537 | 381 |
| TheCryptoconomy | 64 | 142 | 156 |
| Buy2HamsUofA | 64 | 149 | 286 |
| GabBurnett | 32 | 90 | 0 |
| _nicopalavecino | 26 | 99 | 453 |
| jstruhar | 64 | 129 | 718 |
| KryptykHex | 65 | 616 | 88 |
| BrightBoxPC | 5894 | 22 | 4 |
| minstermanw | 33 | 172 | 531 |
| LazyGuyOnABike | 65 | 228 | 109 |
| easternpa | 213 | 356 | 1352 |
| _SKlahr_ | 56 | 265 | 506 |
| StevePrediletto | 432 | 905 | 1451 |
| _hegarty | 397 | 706 | 2920 |
| AMERICANADRENAL | 63 | 52 | 170 |
| tommywatson | 61 | 822 | 44 |
| spencergolden | 210 | 752 | 109 |
| RhysLoaney | 48 | 33 | 573 |
| storm0light | 142 | 397 | 8 |
| Bwya77 | 1385 | 498 | 6003 |
| SirJSDThompson | 600 | 554 | 3091 |
| technocoma | 107 | 197 | 13 |
| LeesKoreaBlog | 10450 | 96 | 3610 |
| bdcravens | 385 | 320 | 3025 |
| judentum1 | 8 | 14 | 9 |
| justinghendrix | 91 | 269 | 6 |
| MuchBitcoin | 1021 | 181 | 10798 |
| RealBenDundee | 252 | 649 | 5282 |
| mpmcsweeney | 781 | 1616 | 6709 |
| woooshtrader | 577 | 149 | 3825 |
| BitConsultants | 362 | 527 | 751 |
| TracyFirm | 5279 | 1951 | 9246 |
| bitcoinvsfiat | 257 | 174 | 973 |
| therealmyownman | 120 | 57 | 74 |
| Edson_VQ | 68 | 330 | 293 |
| jtl999 | 231 | 652 | 6522 |
| flaurita | 178 | 364 | 205 |
| Ginsberg5150 | 828 | 2109 | 4552 |
| Dunne3 | 683 | 2248 | 2311 |
| GianniAvella | 6 | 83 | 4 |
| btcArtGallery | 3796 | 459 | 4530 |
| dbotossi | 16 | 14 | 24 |
| imiragde | 538 | 2154 | 3445 |
| TheDokument | 200 | 391 | 3378 |
| cstutts13 | 70 | 471 | 183 |
| 0daydorpher | 359 | 1484 | 3725 |
| HenkvanRoest | 1678 | 358 | 15346 |
| Moritz30MC | 37 | 201 | 359 |
| radi_v | 70 | 189 | 561 |
| Ralara07 | 74 | 212 | 285 |
| oscardaniel7 | 220 | 307 | 1054 |
| SuomenSuurloosi | 16 | 513 | 1 |
| mikko | 154098 | 777 | 37174 |
| wzulfikar | 62 | 743 | 36 |
| leomangueira | 445 | 2232 | 1728 |
| Teledhil | 41 | 87 | 154 |
| Chocoprada | 389 | 1170 | 3459 |
| issuemakerslab | 1304 | 1662 | 780 |
| fritzfs | 148 | 341 | 1226 |
| flyshuffle | 265 | 580 | 3876 |
| jadastra1 | 2 | 58 | 4 |
| kkc_balaji | 44 | 98 | 63 |
| odoudin | 2860 | 974 | 5155 |
| mecampbellsoup | 530 | 1123 | 1701 |
| realdeerf | 77 | 340 | 381 |
| iv_machiavelli | 243 | 334 | 2332 |
| monkeychief | 316 | 424 | 1825 |
| giuseppegalano | 79 | 277 | 40 |
| benjamindean | 318 | 221 | 1689 |
| RobKeesler | 104 | 36 | 50 |
| Melgorfte | 11 | 30 | 1 |
| fel1x | 5252 | 447 | 61 |
| UlrikUhreBrink | 375 | 727 | 9060 |
| therealvdw | 86 | 202 | 362 |
| brnocrist | 514 | 1652 | 5081 |
| MiKontio | 18 | 163 | 222 |
| TugdualNICOLAS | 720 | 4213 | 1533 |
| IDunWannaCry | 37 | 17 | 75 |
| DrStache_ | 42 | 137 | 6 |
| Rhyzhm | 74 | 1150 | 24312 |
| boh717 | 38 | 234 | 575 |
| FreshHotelEU | 25333 | 2716 | 446 |
| Problem_Ios | 653 | 716 | 4108 |
| samsancho | 123 | 161 | 5334 |
| _jawelin | 41 | 210 | 2883 |
| MoHaMmAd_MaNA | 321 | 1478 | 546 |
| MarkusOlss | 30 | 169 | 100 |
| dsign_space | 77 | 473 | 2062 |
| penispencil | 207 | 619 | 2091 |
| ekoivune | 1865 | 682 | 6107 |
| iCryptoHuMan | 262 | 410 | 391 |
| pr0xy100kup | 3 | 96 | 10 |
| talgya | 528 | 1265 | 5690 |
| TuurDemeester | 19674 | 618 | 16143 |
| krvax | 1398 | 2970 | 28476 |
| Snyke | 1137 | 85 | 693 |
| dominikstraub | 44 | 413 | 297 |
| evanricafort | 1442 | 781 | 2493 |
| redaellimatteo | 188 | 1071 | 685 |
| lonestarcoder | 104 | 632 | 1403 |
| CiaranmaK | 2252 | 3120 | 8455 |
| PranavVenkatS | 856 | 561 | 1177 |
| kevin_bissett | 35 | 2035 | 1256 |
| mikispag | 5288 | 821 | 3170 |

The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Definition and Characteristics Stealth attacks refer to malicious activities that involve intrusions into computer systems without detection or raising alarms.
Sign up to get regular updates about security and special product promotions.
We value your privacy and will only use your email address for sending the newsletter. You can unsubscribe at any time.
For more details, review our Privacy Policy.