
The Psychological Impact of Social Media Intelligence on Cyber Analysts
The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Article form April 2017
I know, I know, you all can not stand to hear yet another 1d10t talking about how they resolve all your issues and here is the update with new signatures and here is our $RandomMagicSolutionToSolveAllYourProblems comments. I said it before and I will say it again, resolving the issues of modern threats is not done via one magic solution, update or any Anti Virus solution (and before you start saying I hate AV companies don’t because I don’t). Malware and threats are no longer found “first” by any virus solution nowadays, people ask how this is true and I will get to that in a second.
In the old days we didn’t have the espionage and computer warfare capabilities that we have since the 2000’s, this fact has lead (i believe) to an ever increasing spiral of new threats, attacks and new infection methods that are no longer detectable using “old science” and this is no “alternative fact”. Signatures and “Heuristics” and “behavioral analysis” no longer is enough, even “sandboxing” has been circumvented by multiple types of threats and malware to avoid detection. There are different reasons for this (as we stated previously) there is a cycle of two different influences that are changing the threat and risk vectors and attacks these are:
If you look at the slide below you will see how the release of new threats in espionage and warfare has resulted in reverse-engineered technology and attacks into the next releases of computer crime based attacks (or so one may be lead to believe). As new campaigns are started and threats and samples are captured and released, these then lead to advances in a new generation of threats that result in new signatures and behaviors that are different that the previous attacks or original samples. These contain recycling of technology leads to ever bigger database that need to be compared to new samples in order to detect them or assess “typical” malicious behavior that was previously observed.
As new technology is created it then leads to new ways of using either old vectors or new modified vectors that have not previously been associated with the old threats. As this cycle continues recycling then results in newer types of attacks that use things like firmware, signals and a continuous modification of social engineering that looks more and more legitimate (real or authentic) based on detailed target analysis and OSINT procedures.
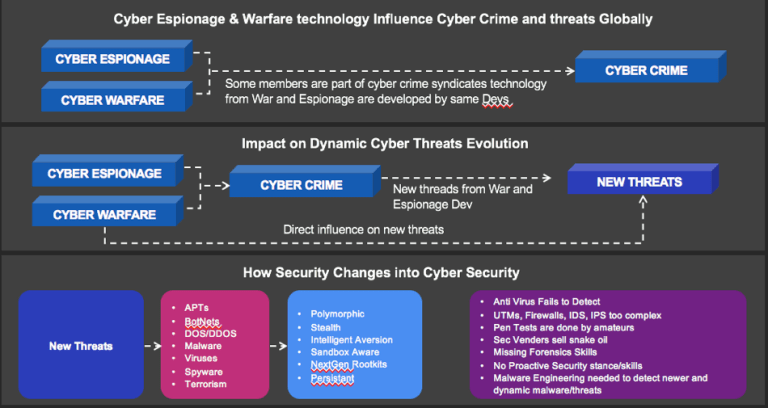
(Sorry btw for the errors in the picture, just wanted to get this out quick to help folks)
If we look at some newer posts from some “security” product manufactures they go on to say that wanna cry was spread by emails. This is false, not one customer of ours has stated that they received the infection via email. Phishing campaigns would be a very critical thing here to prove if the massive infections were actually a cyber war campaign in disguise. Right now we do not have the evidence to support that. I would kindly ask that all the folks posting this type of rubbish please post supporting evidence validated by a neutral party that this was actually the case.
So lets look at how reality stacks up with ransom ware and how many variants are actually out there. To do this we used our dedicated forensics soluiont CyberNsight to find relevant information on ransom ware and known threat and risks that we have in our database (we built this by ourselves and using our solution…). We see some interesting results.
The screenshots are from our solution looking for ransom ware variants, sellers and versions. We are posting this so that security teams that may not know where to find this can use “our” research to help “their” customers be more secure. If you count the different threats and risks only from this “example” of how we proactively look for risks and threats, you will see that you would have to download, infect and create IOCs for “each” entry in this example to say, okay we can give you “some” more security for these risks / threats. However its not that easy. Also if you look at this example of just one place where malware, DDOS, viruses and ransom ware is sold you can see that the risks are much higher than just one “WannaCry” infection. Some of the services sold here are re-cycled older variants of detected malware, ransom ware and viruses that have received new features, functions and also create new signatures and heuristics. We see that this one example shows that Ant Virus can not resolve this issue, the only things that can is proactive security and a combination of processes, procedures, partners and solutions.
We help reduce those risks and the time to find them by up to 90%, thats a lot if you don’t have money, time or the people to do the research. Its impossible if you don’t know where to look, how to look and how to determine if those results are legitimate or fake. Many security people will say I can find that, but this is a BS answer that is also a lie. If you don’t do your research, you have no clue where to look and how to evaluate what you are looking at and for.
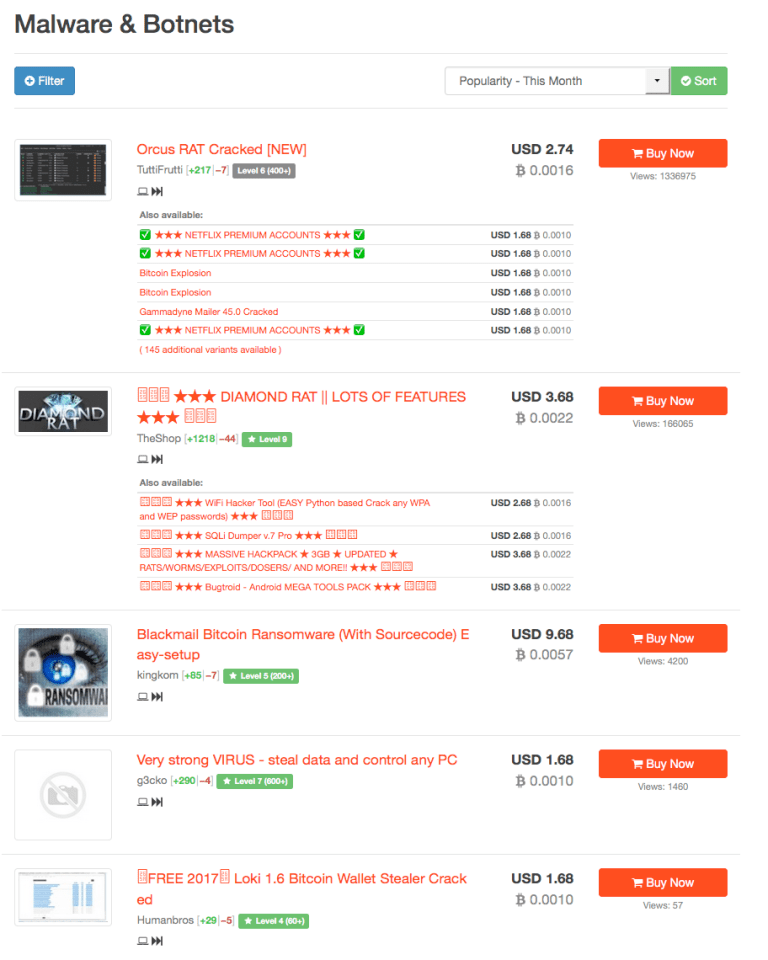


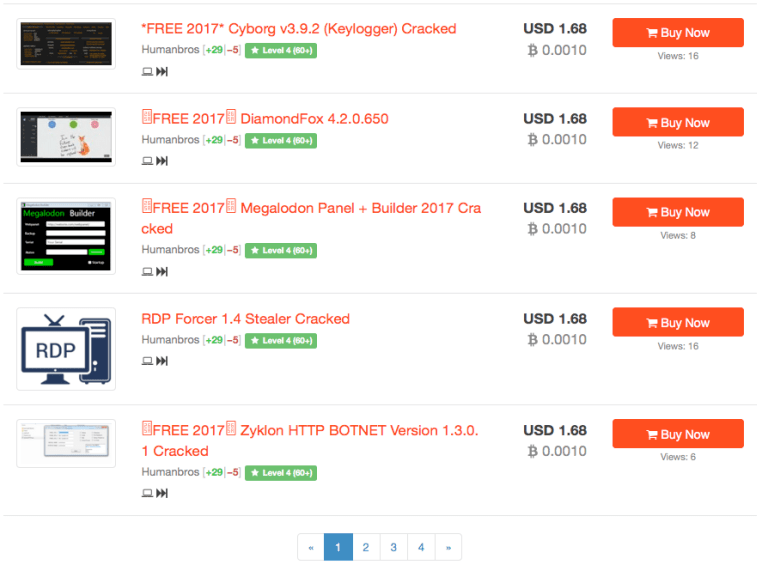


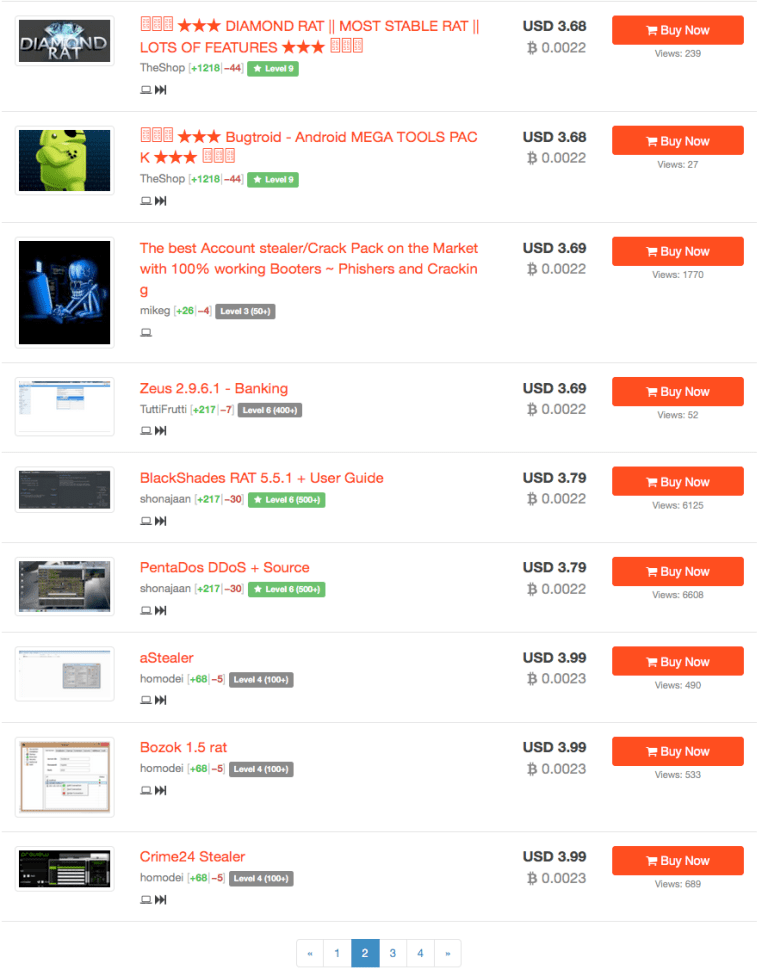
So from the screenshots above we take the following information away:
Our analysis technology can help you identify threats and risks like this using open-source mathematics like bayesian probabilities or neural networks. Its not rocket science (even if the “cybers” say it is). Finding threats is all about finding what is of interest using dynamic and customized detection, basic algorithms and honestly experience in forensics principles and OSINT. You can automate some of this but never all of it, this is where the real solutions are and the fake ones don’t reach. The question I am asked is why is this important? Well lets think about all the systems that COULD have been infected and MAY be infected by the next iteration of “WannaCry”. We can sinkhole domains or detect IPs but this will not show us what is next, who is selling it and how will it evolve. Its about tracking and detecting the unknown. This is were we start our research, it is the only area “we believe” that makes sense before an infection actually happens.
If we look at the example from previously published results of mawaretechblog and malwaretech (previous post), you see a domain. The picture below is someone who tried to take over the domain accidentally discovered….
An example of this detection based on our rulesets and algorithms is here:
We look at various sources of data and information to find something relevant to you, the company or a specific target. Doing this saves so much time and money the return on investment is immediate.
Thanks for reading and if you have any questions please send them to [email protected]
M
This post and all its contents are copyright HDN / Hakdefnet 2017, all rights reserved.
P.S. Interesting fact, about 80% of the attacks on this website that target logon are from China…
IPs below…
| 122.227.168.230 |
| 112.4.117.104 |
| 120.194.173.133 |
| 218.61.30.237 |
| 117.132.12.5 |
| 59.51.162.155 |
| 200.107.7.138 |
| 183.56.157.122 |
| 193.201.225.156 |
Update: All the information and evidence we have collected so far does NOT confirm that North Korea was the attacker. We would like to point out to those “cyber experts” that just as we discussed in this post, technology is RECYCLED!!!! Therefore it is irresponsible to suggest that a specific nation-state is behind an attack UNLESS you have neutral FACTs and EVIDENCE to support that claim. This is exactly why we post some of our research so that you the reader can make an educated opinion about what is going on, how the track, discover and categorize risks and threats and what methodology we use to do that. Claiming something without evidence is just BS and FUD, it helps no one and certainly does not result in additional business…

The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Definition and Characteristics Stealth attacks refer to malicious activities that involve intrusions into computer systems without detection or raising alarms.
Sign up to get regular updates about security and special product promotions.
We value your privacy and will only use your email address for sending the newsletter. You can unsubscribe at any time.
For more details, review our Privacy Policy.