
The Psychological Impact of Social Media Intelligence on Cyber Analysts
The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Since 2015 when we released our detailed reports along with our partners Soc Prime on BlackEnergy3+, the attacks on Ukraine Elections and the details of KillDisk, etc. The world was still a bit calm and attacks were not as complex as they now are.
If you have been following us and me for a while you will know that we have been tracking FancyBear / APT groups for a while and have shown in various reports that there are similarities in the attacks that happened in 2015 un Ukraine, Nov. 8 in the US and also around Europe for the French and upcoming German elections.
In our talks last December at HamburgSides we talked about some details of Social Botnets and how these are used to desalinate false information and are propaganda machines for “interest groups” or “nation-states”.
After some research into botnet attacks and “interesting” outages we saw similar activities in the UK and are seeing increased activities in Europe. Some attacks that come from wordpress and other types of attacks come from Russian, Brazilian and other Asian IPs.
These attacks are some of the activities that we are analyzing. Another trend we are seeing increase (again) are the same types of Phishing attacks that lead to multiple attacks in Ukraine, Germany and the US for known and published DNC, Clinton Foundation and other public groups of interest.
In one of our web searches we have found an interesting server named Fancybear.net which seems to be involved in APT-like attacks that are followed by massive scans and attempts from China, Brazilian, Russian, Ukrainian IP based attackers.
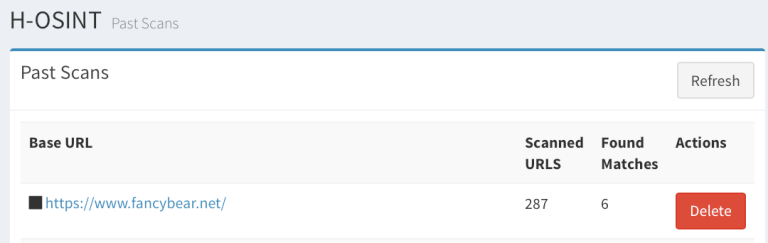
Upon further research we fond some interesting hits on the website that have documents and other objects that are typical for FSB/GRU/APT type of information, disinformation and phishing attacks that have recently targeted multiple elections throughout the world and specifically in France and Germany.
The image below shows some details of the analysis we have done of the server and we have cataloged everything and documented what we have found so far. Since this is security relevant we can not go into more details but it is safe to say that attacks are on the rise again, targets are in Europe and that these are very interesting times.
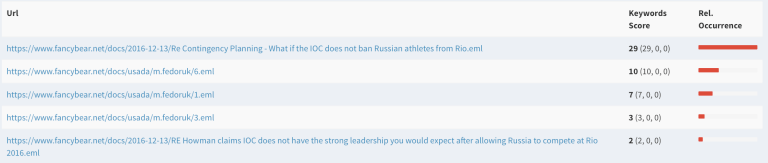
We will keep you all posted about our progress and wanted to highlight that we offer these types of intelligence services and are continuously publishing our research to our sponsors and our subscribers.
Stay alert, don’t open or read any emails you did not initiate.
Regards
M

The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Definition and Characteristics Stealth attacks refer to malicious activities that involve intrusions into computer systems without detection or raising alarms.
Sign up to get regular updates about security and special product promotions.
We value your privacy and will only use your email address for sending the newsletter. You can unsubscribe at any time.
For more details, review our Privacy Policy.