
The Psychological Impact of Social Media Intelligence on Cyber Analysts
The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Article from August 2017
So its been a while since the last post and much has happened, besides the fact that some $Random group as seen fit to install a FinFisher similar “Stealth” interceptor on my Applz Pwn and likely taken snapshots of my awesome body (yeah that’ll break the Internet for sure…).. Anyway moving on..
Today we will talk about the scourge and scurvy of the Internet, Phishing and PhisMarketing. I received multiple emails from $Random legit (yeah sure) companies one of which originated from a website called http://www.globalzestbs.com
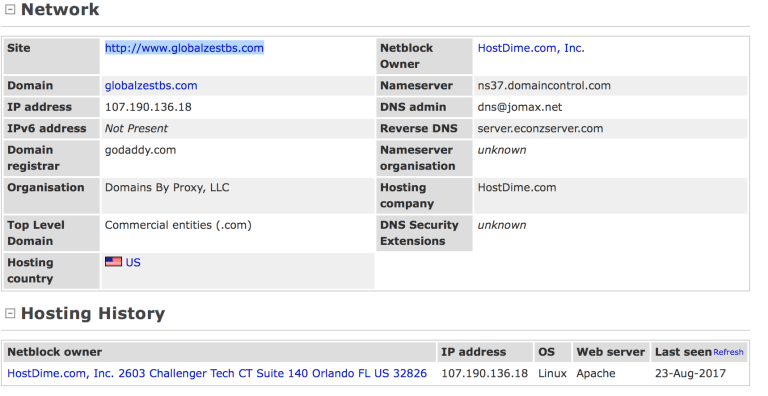
If you are like me and a tad paranoid you want to know who the hell this is and if the person or company is legit so I read this email and think about the recent pwned apple phone I own and thought, lets do some more research and find out who this clown is. So the email trail is started to get them interested..
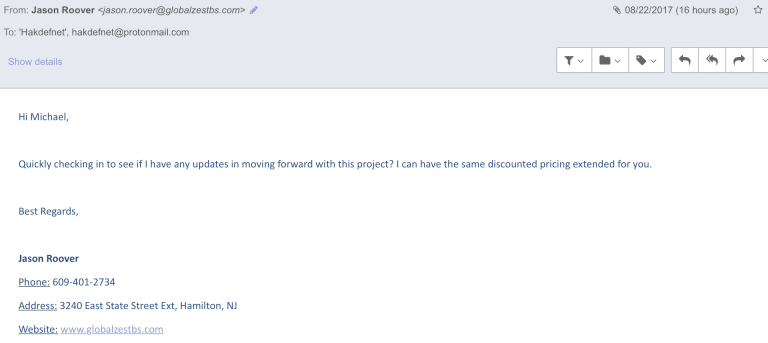
The persons name is Jason Roover and the “email” is [email protected] which seems normal enough. The guy also says he is in Hamilton, New Jersey so lets check this out next.
For some reason the result of the address is this picture which doesn’t really seem to make sense….
This is when it makes sense to check out the details of the email in regards to who this clown really is and what the hell is going on, so I play along and look at headers of the email and get this:
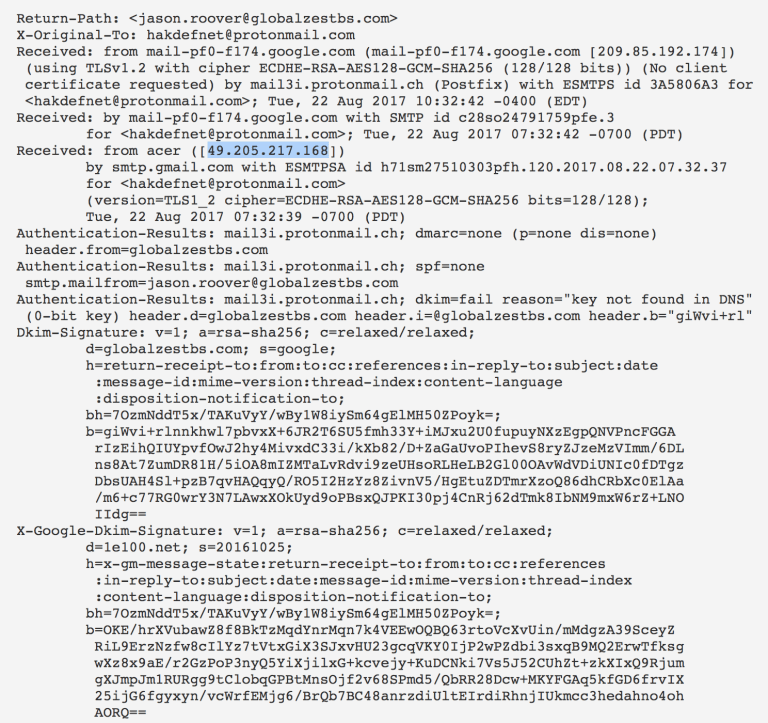
There is a lot of info here and we first need to confirm where the person is coming from, what IP they have, where the email was sent from and all those details to find out if there is in fact a legit person here. Upon looking through the details I find an IP that I can start to trace and verify.
The results are here:
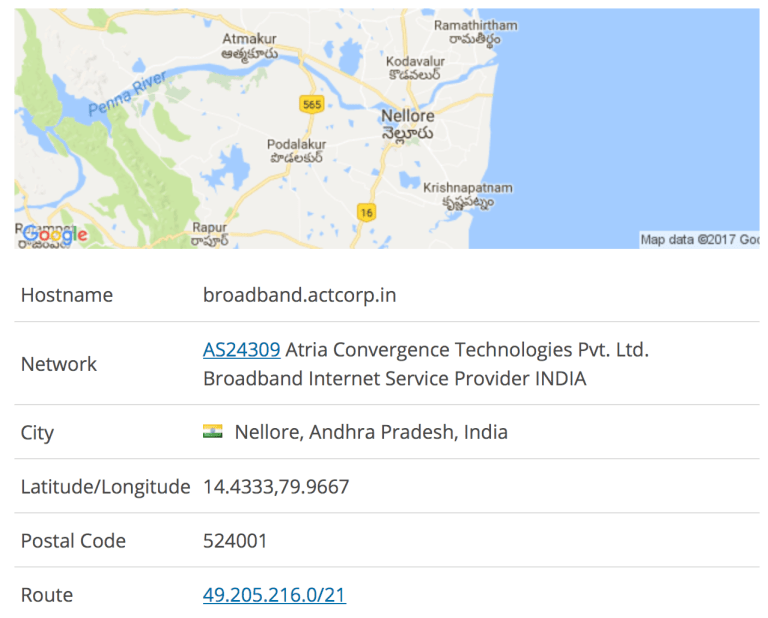
So now I see that the IP is not even from the US (let alone from Hamilton, New Jersey) but looks like it is from India, at this stage I look deeper into the header file and pick out some more red flags. I see for instance the pc name (acer) this clown used and more data about failed DNS and DKIM info which solidifies my suspicions.
And now on for the last piece using CyberNSight. I look at the IP, see if they where involved in any attacks and find the following info out:

If we look further at the IP we will find in a basic NMAP scan (we have this integrated) that the following ports are open (quite a few actually). What i could assume is that this is either a very badly configured server or its been compromised and is being used as a platform for Phishing.

So I hope this short post has given you some points to use CyberNSight in a use case, checking for phishing emails and details. Why? Well to protect yourself against all those bad folks that seek to get your data, information or money for something that is not the value you ay think it is.
The prices that “Jason” was asking appeared very high (more than 1800$) for marketing data that may already be out there for free. If this happens for leads I can only imagine how many “Jasons” are out there pending all kinds of crap to innocent people.
So, be aware, know what to look for and if you liked this, become our customer.
Your 1D10T

The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Definition and Characteristics Stealth attacks refer to malicious activities that involve intrusions into computer systems without detection or raising alarms.
Sign up to get regular updates about security and special product promotions.
We value your privacy and will only use your email address for sending the newsletter. You can unsubscribe at any time.
For more details, review our Privacy Policy.