
The Psychological Impact of Social Media Intelligence on Cyber Analysts
The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
In the last few days I stumbled across an interesting site called cloudflarecock.club. After getting a heads up from a fellow security researcher I decided to have a look and see what was in the domain and what it was all about.
The Picture below shows an initial scan and keyword term analyzing of the website which found multiple hits for Botnet relevant keywords. Our solution has the ability to use multiple types of connections to analyze the website for various types of data.
We also have extensive analysis capabilities that we use to assess risks that others are not currently looking at or can with traditional methods. We figured it was time to add some tangible security to “security solutions” using the lessons learned from my time in the LI industry.
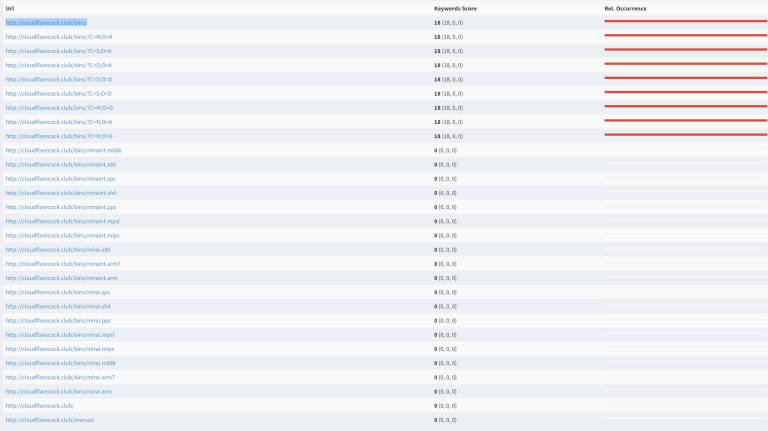
After the initial basic scan I wanted to check out what was actually on the site. In my initial scan I saw multiple pages that warranted a more detailed look and so I found some interesting “deliverables” being hosted on the website that are mire botnet infector related (we saw these before during two other bigger attacks).
The picture below shows the different types of infector / payload stocks that can be used by the team that set up this apache website.
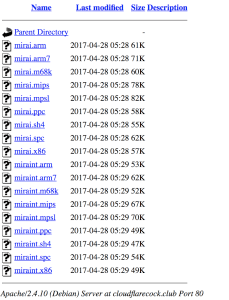
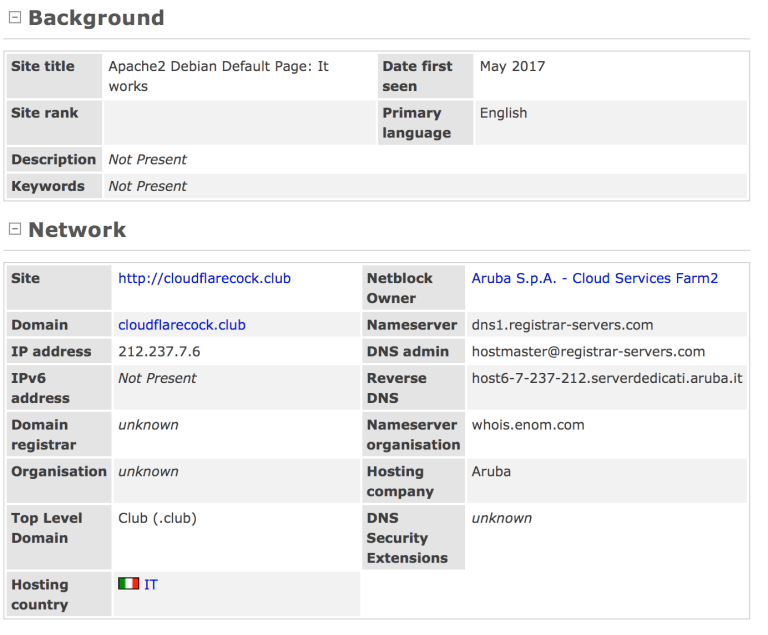
Notice the different types of files that are able to tailor the attack / infection on multiple types of platforms. This website appears to be a new group and likely a skiddie looking to follow the other DDOS type attacks going on in the interwebz that we have seen so far. When looking at details from the website and when it was last seen we see the following results below which would indicate that it is fairly new.
The web server hosting mirai infector files is hosted at Aruba.it in Italy and has an IP of 212.237.7.6
The fact that mirai has caused so much damage shows that we have a long way to go when thinking about implementing new and cool technology that uses linux based busybox or other linux derrivirates that have not been locked down and built for security.
The alarming thing is that there are also firewalls based on busybox linux and may (incorrectly) think that just using Linux is a magic bullet against infections, malware and viruses.
This is simply not the case. The other factor is that many skiddie copycats are diluting the original attackers, making it so much harder to track who is really behind all the mischievous attacks that can easily knock out entire communications and critical infrastructure grids.
Attacks from copycats are increasing, those that are using mirai, brickerbot and the others are using this to stay under the radar and keep folks busy so that they are not at risk of being detected until the attacks have started. Its an interesting situation to say the least. Anyone who says they know exactly who is behind the larger attacks likely does not.

The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Definition and Characteristics Stealth attacks refer to malicious activities that involve intrusions into computer systems without detection or raising alarms.
Sign up to get regular updates about security and special product promotions.
We value your privacy and will only use your email address for sending the newsletter. You can unsubscribe at any time.
For more details, review our Privacy Policy.