
The Psychological Impact of Social Media Intelligence on Cyber Analysts
The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Article form April 2017
“OPERATION DIAMOND EYES”
It has now been a week since all the drama started on a recent attack who’s name I won’t mention anymore because its been milked by anyone and everyone in the “cyber” industry. Theories ranging from North Korea to Internal ruse attacks from national security agencies are out there and being “sold” to anyone that will listen.
In the midst of all this “cyber” bru ha ha we noticed some really interesting behavior checking the DNS records of various companies and critical as well as national security infrastructures that include the German Bundestag as well as European security related domains and also included the FBI (but not the NSA) and many defense near contractors and European companies that may be of interest. What I what to state right off the bat is that this is extremely early stages but we don’t really know for sure who is behind this so I will give everyone that reads this the correct amount of caution. Its bleeding edge and only informational. The info we are giving you needs more research and certainly more validation. So with that disclaimer and anti FUD statement here we go.
We pull in multiple sources of information (open source and own sources) to make sure what we see is really going on. One area that is a bit of a pandora’s box is DNS information, ptr records and a-records. Part of assessing risks is also knowing what your outside footprint is and DNS is a great way to find holes in anyones systems and infrastructure. There are multiple sources of information and we believe that anyone that stores those DNS records is a potential risk because you can use the info for recon on a target.
During searches we found some interesting additional entries pop up from one time period to another. We started queries for some customers and correlated those results with various databases and found the following entries very curious and interesting:
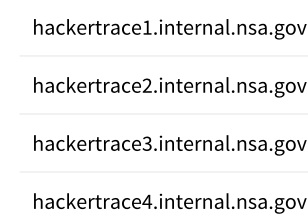
We have only found these entries so far comparing results with ptrarchive.com and not in other returned queries of other open source domain information (so far) so some questions we have are:
So we compared various queries from ptr to see if the hacker trace are on all returned queries and they were not, so we concluded that it was not likely planted by ptr on purpose. If these were faked entries then they should by logic show up in all queries, (they did not). So the question then is are we looking at something real or fake. Right now we believe it isn’t nsa.gov because if they did plant taps into domain searches they should not show up in the open. If these traces are however real then this could mean something very different that another shadowbroker or skiddie planting something. We would be curious to know why domain / dns searches are being tapped by the NSA for companies that are not engaged in espionage or warfare of any kind against the US. Right now there just doesn’t seem to be enough motive to do something this stupid and obvious. When we look at the DNS records for NSA we see nothing close to hackertrace or internal (sorry we are not going to give you those returned results…) so again this “may” mean they are not behind the traces (if they are traces). We also queried critical government sites previously and the last few days like Bundestag, FBI, various defense near contractors and transportation companies in Europe as well as google, etc. They all returned those “curious” entries recently that were not there before. When we queried other companies we didn’t get the same “curios” results but messages that the dns data was stolen (which is curious) because any private server that stores domain information can not charge for it because the dns is by definition open source and the data is not licensable as a product because you would need permission form everyone to do that (assumption that domain data of a person or company is owned by that company or person). Since I am not a lawyer I don’t know for sure but it would be very weird for someone who collects 58 billion entries (dns records) and then says they sell that data for a price without asking the data owners for permission.
Looking at an attempt to see if this is actually part of NSA and assuming the hackertrace is part of the nsa domain I tried to see if there is a website that may be listening for any communication from infected assets or waiting for beacons to call home. A simple look at netcraft shows this result (which basically tells me nothing) except that there is an nsa.gov domain and that hackertrace is likely not part of it.

This brings me back to the other options that this could be a glitch on the dns database we are querying and that it is either being tampered with or legit. I don’t currently have enough details to say its legit so I am assuming that it may be an actual trace.
Since Shadowbrokers is coming up with another release I wonder if they will talk about a new nasa tool that includes hackertrace, if it does we have a good indication that they are planing false information to discredit the NSA (since we found no such domain entry at the NSA). Stay tuned for more information. Whatever you do be very careful with anything Shadowbrokers and Wikileaks information that has not been verified by third parties that are authentic.
M
This post and all the research are copyright HDN, Hakdefnet 2017 (all rights reserved).
(Additional background info and updates)
DNS information for queries were compared with root dns servers and also ptrarchive.com (Currently there are no signs or information that ptrarchive.com has a right to license and charge for dns queries or data).
The picture below shows some details of ptrarchive.com.
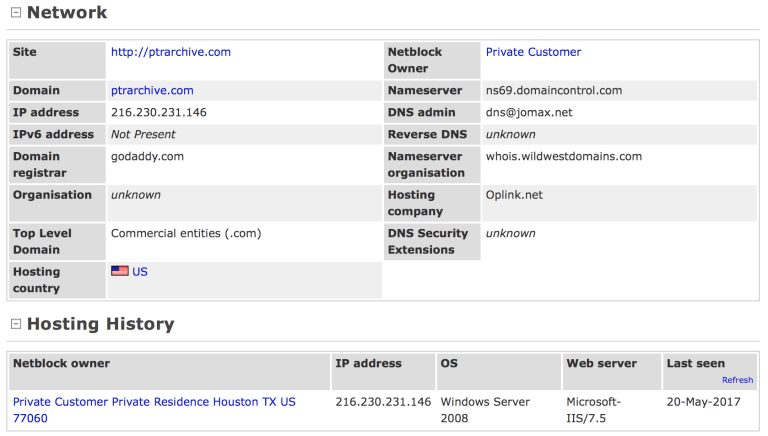
Update: Still getting interesting results from ptrarchieve for instance this VPN service (who’s IPs we have in our database).
| hackertrace1.internal.nsa.gov.northghost.com |
| hackertrace2.internal.nsa.gov.northghost.com |
| hackertrace3.internal.nsa.gov.northghost.com |
| hackertrace4.internal.nsa.gov.northghost.com |
Notice the hackertrace1-4 addition to the domain north ghost.com (is this tampering, a ruleset with queries or actual traces is still unknown. The fact that we see a lot of these now is at the very least interesting…..
So after searching and searching we finally have some new information and it certainly doesn’t look bad. It seems like the entry for domain plus the “curious” entry we found seems to come from rule sets for https everywhere that act as a suspected “sinkhole” for malicious or bad traffic. In this case we have found a rule in https everywhere that contains the hackertrace1-4,internal.nsa.gov here: https://github.com/EFForg/https-everywhere/blob/master/src/chrome/content/rules/mstrok.ru.xml
An example of the usage to use the xml based file is here:
| <!– |
| hackertrace1.internal.nsa.gov.mstrok.ru ¹ |
| hackertrace2.internal.nsa.gov.mstrok.ru ¹ |
| hackertrace3.internal.nsa.gov.mstrok.ru ¹ |
| hackertrace4.internal.nsa.gov.mstrok.ru ¹ |
| w.mstrok.ru ¹ |
| ww.mstrok.ru ¹ |
| ¹ mismatch |
| –> |
| <ruleset name=“mstrok.ru“> |
| <target host=“mstrok.ru“ /> |
| <target host=“www.mstrok.ru“ /> |
| <rule from=“^http:“ to=“https:“ /> |
| </ruleset> |
This could mean a few things as if these are rulesets for https everywhere then they are used to flag malicious traffic or malware activities because the use cases I am seeing are associated with .ru domains that appear to be involved in malicious activities. So either these domains now showing up with query entries are using https everywhere (in which case) the ruleset should look more like this example: https://github.com/EFForg/https-everywhere/blob/5.2.10/src/chrome/content/rules/Google.xml
If we assume its a legitimate ruleset to block domains that are suspicious I could understand something like .ru domains and that the ruleset is used to sinkhole traffic of malicious actors. If this is the case we just found a whole new set of risks that have not even been thought of before. If a ruleset adds for instance hackertrace1.xxx the you can use those queries to see where previous malicious traffic was coming from previously. If this is the case you just gave crackers (criminal hackers) and other folks interesting in “vulnerable hosts” a possibility of identifying any and all infected domains and companies with some sort if malicious activities (unless of course all our queries are now flagged as malicious in which case this would have to be validated).
We are trying to contact the appropriate companies who’s queries came back with the assumed sinkhole entries to determine what exactly is going on. If these are indeed sinkholes they are a big risk as well because then all you have to do is query domains you believe are infected and use that information to start the next attacks because you know some of the weaknesses now. One does have to love RECON and OSINT, it really helps to know possible risks and exploits…
For more information on Sinkholes please read here:
http://someonewhocares.org/hosts/
https://www.sans.org/reading-room/whitepapers/dns/dns-sinkhole-33523
In general DNS spoofing / forging is using DNS query information that may be stored in an authoritative DNS server that returns modified or malicious results of domains to IPs in an effort to send back wrong results or worse, to plant another server or IP in the entry of an otherwise legitimate domain. An example is the following:
With a poisoned DNS server you change the ip to your server:
There are various other additional attacks that “can” be used like adding sub-domains, (support.hakdefnet.com) and adding CNAMEs to existing domains and overwriting an existing authority which can point to an authoritative DNS server that gets information from one of 13 root DNS servers in the world. If you manage to forge the record for that server then all domains that are cached on that server can be forged and changed to point to infector points, network taps and MitM as well as other handy little tricks. The person that is subject to this attack then sees nothing wrong if the attacker does things correctly. For instance you want to intercept someones traffic and reroute them to an infector that can collect data on anything on the computer or network. In this case you could do the following:
If you do not think this is possible please view this little tool that makes DNS poisoning possible via USB sticks and other methods.
Here is a nice little tool that I have used before that is easy to learn, easy to modify and has quite a few modules already created for the Red Team member to use:
https://github.com/gentilkiwi/mimikatz
Additional modules are also available here:
https://github.com/gentilkiwi/mimikatz/releases
For additional information on DNS Spoofing or DNS Poisoning please start here:
https://www.cs.cornell.edu/~shmat/shmat_securecomm10.pdf
https://en.wikipedia.org/wiki/DNS_spoofing
As a bonus here is one of those wannacryp decryptors that you can also try in case you have been infected and have data encrypted by wannacry cronnies:
https://github.com/gentilkiwi/wanadecrypt
Kudos to the user Gentilkiwi!
M

The role of cyber analysts often entails continuous exposure to distressing and harmful content, including violent or explicit material, hate
Definition and Characteristics Stealth attacks refer to malicious activities that involve intrusions into computer systems without detection or raising alarms.
Sign up to get regular updates about security and special product promotions.
We value your privacy and will only use your email address for sending the newsletter. You can unsubscribe at any time.
For more details, review our Privacy Policy.